Have you ever logged in to your WordPress dashboard, noticed that there were some updates pending, but simply couldn’t be bothered pushing the button to run them? Sure you have. Who hasn’t? A good majority of my work comes from dehacking websites that have been compromised, and even I slack on that from time to time. I mean, if there are no security bulletins about the updates, and I am only using plugins I have downloaded directly from WordPress.org I should be fine, right?
Wrong.
The day before yesterday I rebuilt a client’s site that had ben hacked, grabbing fresh versions of all of the plugins he was using. I noticed that one of the plugins, Social Media Widget, didn’t download though, and when I went to investigate why I saw that it had been yanked from the WordPress repositories. Checking Google’s cache I could tell that it had only recently been removed, that the old download button still worked, and there were no warnings or messages as to why it was pulled anywhere I looked. I went ahead and grabbed a fresh copy, then posted on the support forums (which also gave no clues as to why it was gone) asking what was up with it:
http://wordpress.org/support/topic/anyone-know-why-social-media-widget-was-removed
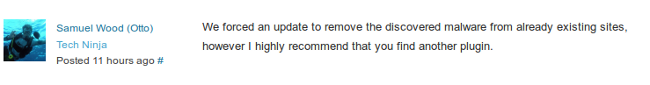
A few hours later I got my answer: the plugin was infected with malware, so they had removed the plugin page altogether. According to Samuel Wood (Otto), one of the WordPress devs, they “forced an update” of the plugin to a version that they fixed:
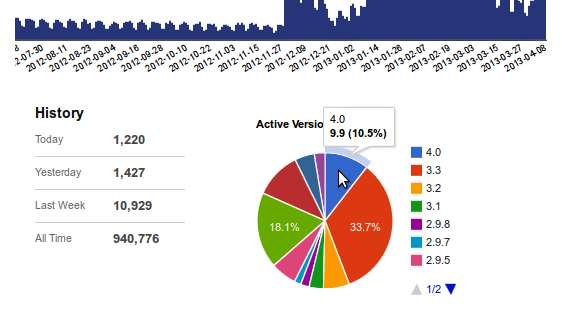
Two things struck me as wrong about this. First, WordPress cannot “force” an update of a plugin to the users themselves, so Otto’s claim was misleading at best. They can only update the svn, which then let’s the user know that there is an update available (assuming that they log in to their dashboard of course). If the users do not see the update, or do not have reason to believe that there is an urgent reason to run it, then it will remain on their installations until they do. To give you an idea of how ineffectual that tactic is, if one relies solely on that for protecting the infected blogs, here is a screenshot of the distribution of the various active versions of the plugin from back on March 28th:
This shows that less than 10% of the almost 1 million users had upgraded to the most recent version of the plugin, which had been out for a month when this data was collected.
Second, why is it that until I actually posted this question, no word about this infected plugin was mentioned by WordPress? There was nothing on the WordPress.org blog, nothing on Twitter from any of the developers, nothing on the plugin’s support forum, and of course, aside from letting me know that there was an update, nothing in the WordPress dashboard, not even when I clicked on the “View version 4.0.1 details” link in my plugins screen:
In fact, the only place you will see any information related to this malware is if you run the update, navigate to the folder for the plugin, open the readme.txt in there, and scroll down to line 181:
== Changelog == = 4.0.1 = * Remove potentially malicious code.
And that’s the extent of what WordPress feels is necessary to warn it’s users that there was a exploited plugin that was distributed from the official plugin repositories. This isn’t one of those obscure, rarely used plugins, either. Before being yanked this plugin had been downloaded 940,776 times. Currently the remote file that was being included in the plugin merely contained some spam, and associated Javascript to hide the spam from normal view, but since the remote file itself is under control of someone who obviously is not brimming over with moral fortitude there is nothing saying that they couldn’t decide just as easily to swap the file out for something that spreads viruses. In such a case that would mean that everyone still unaware that they are hosting an infected plugin would suddenly be serving viruses to their audience. If you ask me the fact that there is a chance that could happen should be enough to put out a tad bit more of an alert than a single line in a reademe.txt that the majority of people will never read. WordPress, however, doesn’t seem to feel that way.
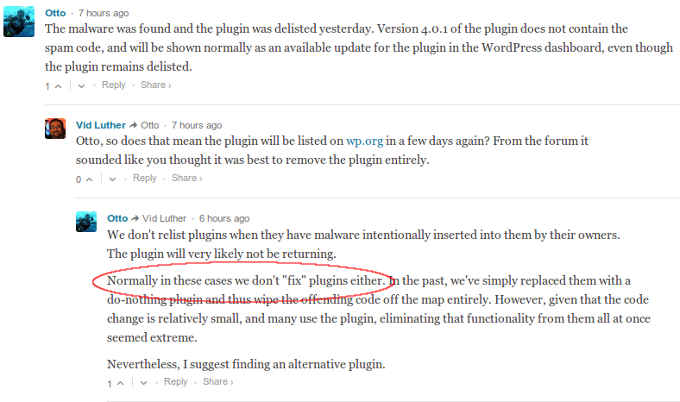
Even more disconcerting is what I found out a little bit after that. Once I got my answer in the thread I opened, Sucuri blogged about it, and Samuel left a few comments there as well, where he used the phrase “Normally in these cases” when referring to this incident:
This tells me that, regardless of how rare it happens, it appears to be WordPress’s policy that when an infected or compromised plugin makes it’s way into the repositories they quietly clean it up without any fanfare. Often times, unfortunately, this would be like closing the proverbial barn door after the horses got out, and stronger measures may be necessary (up to and including rebuilding the whole installation in some cases). The WordPress plugin repositories are supposed to be a trusted source. Not being more forthcoming when something like this happens borders on negligence, to put it bluntly.
I understand that in years past WordPress had quite the reputation as being a security risk, and that there is a certain amount of bad press associated with being upfront about incidents such as this. However, I hope that WordPress will eventually decide that potential public safety risks outweigh not wanting to look bad, will do the right thing, and will change their policies about publicly letting people know when these things happen.
I’m glad WP.org can’t remove plugins from my sites. If it was possible, I imagine you would just find a way to leverage that in your 100% GPL compatibility argument of years past. Haters gonna hate.
Cory, sorry, you lost me. Did you think I was saying it was a bad thing they couldn’t make changes on your site without permission…?
This is pretty scary – I have fixed a few infected sites recently, but don’t always strip and reload the plugins.
Their handling of it though is troubling for a platform that is so common…hope to hell the spammers didn’t see that exchange, or I can imagine even more exploits.
Yes. It seems like you’re upset about two things:
* that WP.org can’t force updates
* that WP.org isn’t blogging about bad plugins
“They can only update the svn, which then let’s the user know that there is an update available (assuming that they log in to their dashboard of course). If the users do not see the update, or do not have reason to believe that there is an urgent reason to run it, then it will remain on their installations until they do. To give you an idea of how ineffectual that tactic is, if one relies solely on that for protecting the infected blogs, here is a screenshot of the distribution of the various active versions of the plugin from back on March 28th:” [picture of old versions being used]
This paragraph makes it seem like you want forced updates.
No, that’s not what I was saying at all. You need to look at that in context to what Otto said, ie. “we forced an update to remove the discovered malware from already existing sites”. I was pointing out that to those who didn’t know better Otto’s statement might sound like “don’t worry, we handled it and fixed the infected sites”, when in reality they did not, because they could not. I was not implying that they should be able to do that, but the fact that they can’t fix this for people is why they need to be telling them about it.
Ok. I disagree. WP.org blogs less than once a month, and you’re asking for an order of magnitude increase to include security bulletins. I think the volunteers have more important things to do than blog warnings to people who don’t read warnings. Your picture of version fragmentation above is a clear indicator of why a blog post wouldn’t make a meaningful difference.
To be clear, I disagree that “they need to be telling them about it.”
@Martypants – apparently not notifying the public when there is an issue has been their policy for a while. I found at least a couple more, eg. here and here. It would be great if WordPress would just release the list of plugins that were removed for security reasons on an ongoing basis.
Michael:
Here’s another interesting case where abuse of the system was allowed to prevent a bad plugin from spreading:
http://yoast.com/wordpress-plugin-update/
That is interesting, thanks. I didn’t realize he had done that with the BlogPress issue. And regardless of how you feel about him “abusing” the system (and yes, I would agree he used a “loophole”, although I personally don’t condemn him for it), he does go for full disclosure while doing it. I even think the killswitch option he discusses (ie. being able to “force” updates like we discussed) might be viable, if, and only if, it were an opt-in process. WordPress installs with it off, and you have the option to allow them to kill malicious plugins on your site. Even if that did happen though there should be big red alerts in your dashboard if it ever happened, not just the plugin quietly replaced witha dummy version.
As to your earlier comment:
A) I never said it needed to be on their blog, a dedicated feed to just security bulletins would be better.
B) It’s not “to” a specific set of people, it’s to the WordPress community. A particular individual who doesn’t log in to WordPress will still see Twitter, have friends, employees, etc. It’s about not deliberately being hush hush.
C) If you think that this stuff happens enough where warning people would be an “order of magnitude” increase in communications then that increases the importance of doing so. I am pretty sure the frequency of these incidents is not that high though, to be honest. Still, even if it’s only a few times a year the community should be notified.
Seriously, warning the WordPress community about malicious plugins is the responsible thing to do and would actually help their reputation, not harm it. I would wager that WP has a bad reputation as a security risk BECAUSE they don’t do enough to communicate to the community about security issues related to infected themes and plugins. As you said, the WP.org site is supposed to be a safe place to download themes and plugins. If you can’t trust the stuff you download from the official site then who the heck can you trust?
Hmmm that’s quite worrying. I’ve got the AntiVirus plugin installed across all my sites but my understanding is that is really to check the theme for viruses rather than malicious plugins. Can anyone confirm that’s the case?