 Ok, so I just had 2 of my WP installs hacked, on 2 different servers. This is not the same thing that Shoemoney reported on a few days back (hidden link injection), and as of yet I have not seen any definitive answers as to what it is. All of my blogs were upgraded to 2.3.3 last month, and in all but 2 of them the only thing that was kept was the database… the sites themselves were moved to completely different servers in fact, with clean installs.
Ok, so I just had 2 of my WP installs hacked, on 2 different servers. This is not the same thing that Shoemoney reported on a few days back (hidden link injection), and as of yet I have not seen any definitive answers as to what it is. All of my blogs were upgraded to 2.3.3 last month, and in all but 2 of them the only thing that was kept was the database… the sites themselves were moved to completely different servers in fact, with clean installs.
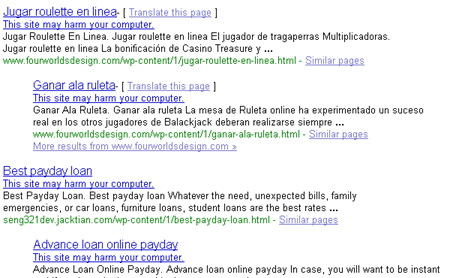
Whereas the WP exploit that Shoemoney and others reported on allowed an attacker to bypass the nofollow routine, and inject search engine friendly spammy links into your comments that were hidden via a <noscript> tag, this one actually creates an entirely new directory, /wp-content/1/, and loads it full of spammy html files containing Javascript redirects in them. You can see the number of affected blogs that Google has already indexed via this query: inurl:wp-content/1/ (cached version).
Please note that I do strongly advise any non-tech savvy people refrain from visiting any of the infected pages listed in those serps, or on their own blogs if they find that they have been hacked. As reported by this blog, at least one of the pages redirects you to a fake Google login screen as a phishing attempt. I have not gone through the other pages myself yet, so therefore have no idea whatsoever what other bits of nastiness they might be holding or might attempt to do. Yes, in general phishing attempts are easy to spot, but not everything that can be maliciously delivered via a webpage is. Also, notice in the search results, Google has already flagged some of these new pages as harmful, but a lack of a flag does not make them safe:
It is better to check your blog for the existence of the directory though FTP.
Apparently the hackers are spamming comments in posts as well, and pointing links at the now infected blog pages to get them spidered and to get people to visit them… such as what they are doing here on this post on SearchEngineJournal, (look at the last comment):
This issue was already reported here on WordPress.org, and whooami claims to have fixed the issue for the original poster on his her blog here and here. However, his fix is based around renaming the cookies used by WordPress by default, and he does make the disclaimer that is he not a developer. If the exploit is hacking the cookies, and whatever current bot is looking for a specific cookie name, then yes, that would stop what is out there now… but it would not fix the issue.
As of this writing I could not find any actual solutions to this, so if anyone figures out exactly how the attack is being carried out please let us know.

Yes, in the posts, not the comments! Anyone else seen this?
Richard – I wasn’t asking a question, I was making a statement. Everyone sees that, it’s how the attack is carried out. 🙂
is this problem in version 2.5.1
@raydo – no, it is not. Did you have a 2.5.1 installation that got hacked…?
If you got attacked, check http://www.bloggerguide.net/blog-platform/wordpress/wordpress-exploit-giving-backlinks-redirects-and-headaches-but-no-visitors/ too. Still working to see where the problem comes from and what tha attacker finds vulnerable.
1 of my website got attacked too. and its wp 2.5.1
anyway, guys make sure your wp-content has a file .htaccess
and contains
IndexIgnore */*
so hackers wont be able to browse on your /wp-content/plugins/ and then check if your site can be hacked using some of your plugins.
Thanks for the post Michael 🙂
fedmich, you can also simply turn indexing off altogether in that directory (or all of them) using .htaccess like so:
Options -Indexes
That’s recursive, so it will apply to any directory under the directory you put it in, unless that directory overrides it using it’s own .htaccess file.
Note, though, that (and the one you suggested) just pertain to directory browsing. If a plugin has a specific file that could be looked for directly, it could still be detected.
As to getting hacked on 2.5.1, yeah, I did as well. 2.5.2 was a security upgrade iirc. I just didn’t blog about that one. It wasn’t as widespread and I didn’t have time when it happened.
How can WordPress be so vulnerable? I don’t get it.
May be due to the theme we used…….don’t know why actually…….but the same thing happened to me too…..but managed at last…….may be this is due to the version.
Had the exact same problem on a 2.7.1 install. Turns out, it was a trojan virus on one of the laptops accessing wordpress.
We changed the root, and user passwords, the files went away.
Actually WrathChylde, I am not sure what you are talking about. changing passwords would not cause the files to be deleted.
Well the popular the software become more hacks you will see. I am happy i opt for wordpress. Was hacked just once that too because i didn’t updated it for more than an year.
We should look at Drupal. Everyweek there is some new vulnerablity patch.