 Over the past few weeks I have noticed a sharp increase of scammers trying to get my Facebook password, and not too long ago a few people I know actually fell prey to it. Recently there was an outbreak of of similar activity on Twitter, where the attempts were being spread through direct messages, and Myspace has seen it’s share of woes with these issue as well. The methods being used to try and trick users into giving their passwords away are collectively known as phishing attempts, where the members of the site are sent a message, either through the site itself or in an email, that contains a link or instructions that if followed result in their passwords being given away.
Over the past few weeks I have noticed a sharp increase of scammers trying to get my Facebook password, and not too long ago a few people I know actually fell prey to it. Recently there was an outbreak of of similar activity on Twitter, where the attempts were being spread through direct messages, and Myspace has seen it’s share of woes with these issue as well. The methods being used to try and trick users into giving their passwords away are collectively known as phishing attempts, where the members of the site are sent a message, either through the site itself or in an email, that contains a link or instructions that if followed result in their passwords being given away.
The sites in question will occasionally give out warnings or advice to their users about not entering in their passwords except when actually on their sites, which is of course what you are supposed to make sure you are doing. The problem, however, is that the warnings hardly ever go into detail about what they actually mean by that. Most of us in the IT field, or people who use the internet frequently and have been doing so for a long time, just assume that everyone we say that to knows exactly what we are talking about. However, multiple conversations I have had with friends on the phone in the past, where I was trying to walk them through installing anti-virus (for Windows users I recommend Avast, by the way) clued me in to the fact that for many people simply saying “Make sure you are on the site you think you are” won’t be enough:
Me: Ok, type this into the address box: a – v – a – s – t – dot com. Then hit Enter.
Friend Ok, done.
Me: Good. Do you see the download link…?
Friend: No. I see… (at this point they start reciting what sounds suspiciously like search results)
Me: Wait… are you in Google? Did you type what I said into the search box?
Friend: Yeah, isn’t that what you said?
Me: No, I need you to type it into the address box, so that you don’t accidentilly click on an ad for a different product.
Friend: Oh, ok. (pause)
Friend: Where is that?
After this happening more than once I decided that a visual tutorial on how not to get hacked on Facebook might be needed.
It’s only a Facebook account, why should I care about security?
Glad you asked. While it is true that sites like Myspace and Facebook are more for entertainment and socializing than for business, and you usually aren’t doing anything extremely sensitive (like banking or dealing with medical records) on them, there are still some very solid reasons to keep your information secure:
- Stolen Passwords mean stolen identity
- Many people re-use their passwords everywhere
- More personal information is collected every day than many people realize
While it is true that most scammers who steal your password do so in order to send out spam, there really is nothing stopping them from using it for more devious reasons instead. True, you usually don’t store your credit card info on your Facebook account, but disguising themselves as you could still be used to scam people who trust you (Your favorite grandson sent you a message on Facebook: “Grandma? I’m stuck in Houston and my phone is dead. Can you wire me some money please?”).
This is not a good idea, but it is a reality. Most of these sites use your email address as your login. If you happen to use the same password for your email as you do for your social media accounts, then this gives the hackers access to all other accounts that you happen to have used that email for, even if you used a different password, since all they have to do is hit the Lost Password link and then log in to your email to get the new one. As a side note, the password generator I built can help with this, since it is generates easy to remember passwords, making it easier to maintain different passwords for different accounts. At the very least your email password should be unique and hard to guess, since that is in essence a master password for all of your other accounts.
Recently there has been a fuss about the new Facebook privacy settings, and what you can and cannot make private. It is the belief that their information is private that lured many people into giving away more info than they probably had intended. If someone gains your password then it of course won’t matter what your privacy settings are, they can just browse your account (and private messages) at their leisure.
Here are some visual cues to let you know whether or not the link you clicked on is really what it seemed to be.
Look at the actual address bar to see what website you are really on.
An easy way to know where to look when looking at a web page address is to remember that the address bar is not located on the actual webpage. It is part of the browser window (Internet Explorer, Firefox, Safari, Chrome, etc.) itself. It’s located at the top, in the section that has the exact same layout and look and feel regardless of which webpage you are visiting. It is usually above any toolbars you might have installed. It is also distinct from any search boxes that a toolbar or browser may have:
In Internet Explorer 8 the address bar looks like this:
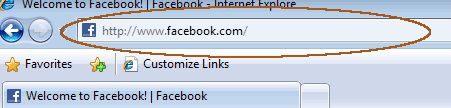
Look at the address again… closely.
A url (or webpage address) is composed of multiple parts. The first section of the url is known as the “domain”. This section is always located between the “http://” at the beginning, and the very next forward slash (“/”) that you see. For instance, the domain you want to be on when logging into Facebook is “www.facebook.com”. The “www” portion may change, but if you see anything between the “.com” (or “.net” or “.org”, etc.) and the next slash, then the site is not what it is pretending to be:

Some other quick visual cues that might help:
Does the message really sound like your friend?
In most cases when an automated message is sent from a hacked account it is either the same message sent to everyone, or it is a small set of short messages pulled from a library. The most common are probably messages asking “is this you?” and referencing a picture or video that has supposedly been posted to the internet. In a setup like Facebook’s, where you not only see what messages are sent to you but can also view your friends other publicly posted messages, you can often tell that someone’s account has been hacked because they will start sending a series of odd or repeated messages, all containing links:
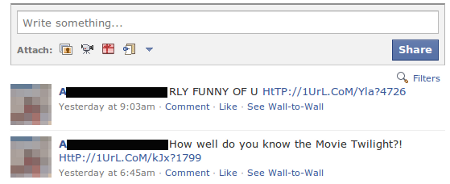
If the link was in an email from the website, does the sender’s address look right?
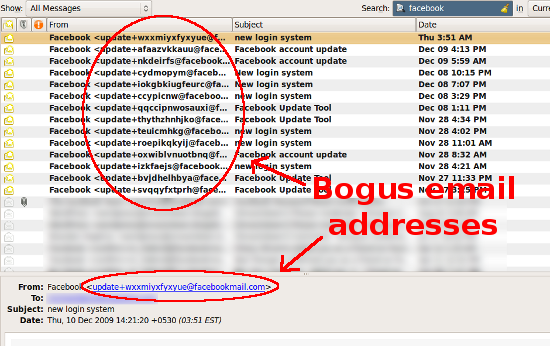
Not all phishing attempts are going to come from people on your friends list. Sometimes scammers will send out mass emails pretending to be from the social websites themselves. While the actual From field in an email can be faked, often times in these cases they are not forged properly. Any emails from Facebook, for instance, should actually have “@facebook.com” in the email address, and not random characters or be from Hotmail:
Are there any mistakes on the login page?
It is of course possible to make an exact perfect copy of a login page for any given site, but not all hackers bother to do so. Take a quick glance at the page before logging in. For instance, you might see an extra less-than sign, like in this fake Twitter login page, which is usually a sign of broken html somewhere:
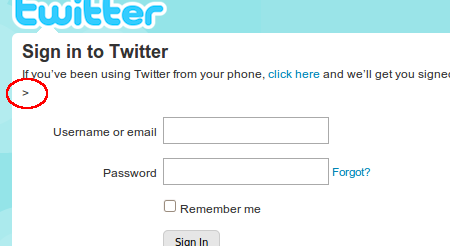
And major social media websites are never hosted on free hosting accounts, which usually add in their own text or ads to every webpage:
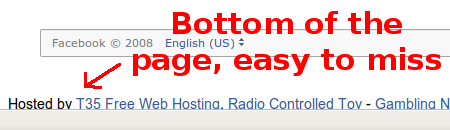
And lastly, one of the biggest clues that a login page is fake…
Were you logged in before you clicked on the link?
Except in households where more than one person has an account on a particular social medial site, or in cases where you are logging in from a public (or work) computer, most people simply never bother logging out of the site. If you are reading a message someone sent you on Facebook itself, then you have to be logged into Facebook in order to read it. If the message asks you to click on a link, and the page it takes you to asks you to log into Facebook again, then something is wrong.
Hopefully these simple tips will help some of you from giving away your accounts, even temporarily, to people you would rather not give them to. 😀
I want to thank you for writing this. Excellent reference and resource. I’m going right now to follow you on twitter.
Not to be a bummer, but the best way to avoid Facebook, Twitter, Myspace hacking is to simply not to use the sites. For most sites there are far better ways of networking and promotion. Than playing around on these social media sites.
@Seattle SEO, it’s not being a bummer, but you need to understand that 99+% of the people on those sites are not marketers or seo’s, and are not there for promotion. This post wasn’t written specifically to the marketing community, it was written for anyone having a social media account.
Appreciate the info
tried to subscribe to your feed, but need help with that please
thanks
Even worse, please do not even click on the link at all, as doing so can still download a trojan to your PC.
I host other peoples websites, and unfortunately see this happen on a regular basis.
The fake login pages include a method to automatically download a very small hence quick exe program that will turn your PC into a bot for spammers, and sometimes a keylogger to steal all your passwords.
Just delete these emails immediately.
If you hover over the links in their email, it will give you a clue that it’s not the original website and therefore a phishing site.