 Getting hacked sucks, plain and simple. It can affect your rankings, cause your readership to be exposed to virus and trojan attacks, make you an unwilling promoter to subject material you may not actually endorse, and in many cases cause the loss of valuable content. However, once it happens it is usually best to not procrastinate on the clean up process, since a speedy restore will most times minimize the damage that was caused.
Getting hacked sucks, plain and simple. It can affect your rankings, cause your readership to be exposed to virus and trojan attacks, make you an unwilling promoter to subject material you may not actually endorse, and in many cases cause the loss of valuable content. However, once it happens it is usually best to not procrastinate on the clean up process, since a speedy restore will most times minimize the damage that was caused.
While almost all sources will recommend that you upgrade your WordPress to the latest version, what the majority neglect to tell you is that in most cases simply doing so will not prevent the attackers from getting back in, even if there are no known exploits with the latest version. The hackers may have left a back door file hidden in a directory where it wouldn’t get overwritten with an upgrade, or inserted code into your theme, or simply created an account that they then granted admin privileges to. Any one of those would allow them back in, even after you patched what was wrong the first time. Therefore I am providing this step by step process on how to completely clean out and restore a WordPress installation that has been hacked.
1. Backup the site and the database.
Even a hacked copy of your blog still probably contains valuable information and files. You don’t want to lose this data if something goes wrong with the cleanup process. Worst case scenario you can just restore things back to their hacked state and start over.
2. Make a copy of any uploaded files, such as images, that are referenced.
Images are generally exempt from posing a security risk, and ones that you uploaded yourself (as opposed to ones included with a theme, for instance) will be harder to track down and replace after things are fixed again. Therefore it is usually a good idea to grab a copy of all the images in your upload folder so as to avoid broken images in posts later. If you have any non-image files that could potentially have been compromised, such as zip files, plugins, or php scripts that you were offering people, then it is a good idea to grab fresh copies of those from the original source.
3. Download a fresh version of WP, all of the plugins you need, and a clean template.
Using the WordPress automatic upgrade plugin does make it easier to upgrade every time a new version comes out. However, it only replaces WordPress specific files, and does not delete obsolete ones. It also leaves your current themes and plugins in place, as is. This means that if used to upgrade a blog that has already been compromised, it can very well leave the attackers a way back in. It is best to start over from scratch as far as the files portion of your installation goes. Note that if you use the EasyWP WordPress Installer script that I wrote it saves you from having to download, unzip, and then upload all of the core WordPress files, although you will still need to grab fresh copies of the themes and plugins that you want to use.
4. Delete all of the files and folders in the WP directory, either through FTP (slower) or through cPanel’s File Manager (faster).
Now that you have fresh copies of all the files you need, and copied all of your uploaded images, completely delete the entire directory structure your blog is in. This is the only surefire way to completely remove all possibly infected files. You can do this through FTP, but due to the way that FTP handles folder deletion (ie. it walks the directory structure, stores each and every file name that needs to be deleted, and then sends a delete command for each one), this can be slow and in some instances cause you to get disconnected due to flooding the server with FTP commands. If available it is much faster to do this through either cPanel’s File Manager, or via command line if you happen to have shell access.
5. Re-upload the new fresh copies you just grabbed.
This step should be self explanatory, but I would like to mention that if your FTP client supports it (I use FileZilla, which does) and your host allows it, then increasing the number of simultaneous connections you use to upload can greatly reduce your overall transfer time, especially on servers or ISP’s where latency is more of an issue than bandwidth. In FileZilla this setting is found by going to “Edit -> Settings -> File transfer settings”:
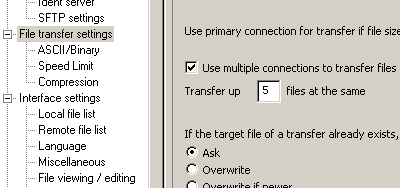
Also, if not using the EasyWP WordPress Installer script, don’t forget to edit and rename your wp-config.php file (when freshly unzipped this is named wp-config-sample.php).
6. Run the database upgrade (point your browser at /wp-admin/upgrade.php).
This will make any necessary changes to your database structure to support the newest version of WordPress.
7. Immediately change your admin password.
If you have more than one admin (meaning any user with editing capabilities), and cannot get the others to change their passwords right then, I would change their user levels until they can change their passwords as well. If there is anyone in your user list that has editing capabilities, and you do not recognize them, it’s probably best to just delete them altogether. If changing passwords is something you hate doing, then maybe my new memorable password generator can make that a little less stressful for you. 😀
8. Go through the posts and repair any damage in the posts themselves.
Delete any links or iframes that were inserted, and restore any lost content. Google and Yahoo’s caches are often a good source of what used to be there if anything got overwritten. The following query run against the database can help you isolate which posts you want to look at:
SELECT * FROM wp_posts WHERE post_content LIKE '%<iframe%' UNION SELECT * FROM wp_posts WHERE post_content LIKE '%<noscript%' UNION SELECT * FROM wp_posts WHERE post_content LIKE '%display:%'
If you did not change the default prefix for WordPress tables, than you can copy and paste that directly into a query window and run it, and it should pull up any posts that have been modified to hide content using any of the methods I have come across so far (iframes, noscript tags, and display:none style attributes). To get to a query window in cPanel, you would click on the MySQL® Databases icon, scroll to the bottom of the page, and then click on phpMyAdmin. Once the new window or tab opens, you would click on the database in the left hand side that your blog was in, and then in the right side at the top click on the SQL tab. Then just paste the query into the large text area and hit the Go button.
Note, however, that there may be other types of injected content that I haven’t seen yet, and that a manual inspection looking for the types of patterns that first alerted you to the fact that your blog was hacked is always a good idea.
UPDATE: 9. (still valid in 2015) If you are having issues cleaning the installation yourself
When I wrote this post back in 2008 I intended it to be a do it yourself guide for the non-techie. However, I do realize that some people would still rather a professional programmer perform many of the steps I outlined here. If anyone has had their WordPress installation hacked, and either is uncomfortable attempting to clean it on their own, or has tried to do so with no success, I am available on a case by case basis. Most cleanings can be performed in about one hour, two at the most. The time can vary depending on the size of the blog, the amount of customization to the original theme, and the number of plugins installed. Feel free to contact me here if you feel like you could benefit from my help. Please include the site and any details that you think might be relevant (pro theme, anything you may have tried on your own, etc.) in the contact form.
UPDATE #2: 10. A note on hosting.
This past year (2010) has seen multiple waves of attacks on people’s websites that happened not due to insecurities within the WordPress platform itself, as has historically been the issue, but rather due to vulnerabilities with the actual hosts. Some of the bigger names that were hit include GoDaddy, Rackspace Cloud, MediaTemple, and Network Solutions, for instance. It is very important that you use a host that is not only well versed in security, but one that is stable and has knowledgeable tech support as well.
Update #3 11/14/2012:
Please note: if you are currently hosting with either HostPapa or Netregistry and you are here because you were hacked then the following tutorial may not be sufficient. Please see this post for more details:Hosting with HostPapa or Netregistry and Hacked? Switch Hosts Now. (hacked by hacker)
My personal recommendation for shared hosting is Hostgator. It is where this blog and many other sites of mine are currently hosted. Yes, that is an aff. link, but I would recommend them even if it wasn’t. For a dedicated solution that is both affordable and robust I use The Planet, which is where I host Bad Neighborhood. Both companies are ones that I have been using for years without issues, and that I do recommend to my own clients when they find themselves dissatisfied with their current hosts. If you were hacked, and your WordPress was up to date when it happened, then a change of hosts is something you should consider looking into.
nice post,I experienced the same with my blog
Our company has several sites down right now so reports are flying and i’ve sent this blog to the boss..
My wp site was hacked first time but I have cleared it and uploaded freshly again it was hacked after a day and have no clue how to recover my site. I am using latest version 3.1 but no security in my site. How can I stop these BS hackers?
This post definately saved my ass!!
I had recovered my blog which was hacked by this filezilla trojan (on my PC).
Thanks again!!
Amazing work man, I can’t believe it’s this easy- I was spending weeks trying to test my server for hacked files but that’s a nightmare- this eliminates hours of hell and the feeling of “clean” afterwards is much better htan “I hope it’s clean”
Yaeh, Im in the same hot sauce,got hacked ok was cool with it got hacked again. This time it too me sometime to find out that the infection was in the wp-content/themes folder. So now I am ready to reinstall…grrr!!!!
Hi Mike –
I know this post is an old one but want to find out if you could help me with this. I am using RPC protocol to publish posts on to my word press site from a small program that we built. I want to set permalink from my program thru RPC protocol. Is it possible? Can you please guide me in this regard? Thank you -Mady.
Mady, honestly I would have to investigate further to see what would be involved. Hit me up through my contact form if you would like to discuss it further.
Hi there, and thank you for this post. I was hacked today, and after working with my web host all day, they think only my wordpress password was hacked. I did delete the users and blog posts added by the hackers added to blog, but I am not comfortable just thinking everything will be ok now. I think my best course of action is going to be to completely re-install WordPress all the plug ins and my theme. My question is two-fold:
1. If I use WP Import after the new reinstall to “import” the files I backed up today, do I risk re-infecting my site? Can the hackers have inserted malicious code there? and
2. In your step No. 4- delete all files in the WP Directory. Can you be more specific, or clarify “WP directory” for us idiots? Suppose I use the “FTP” method, do I just delete every single file and folder under “mysiteurl.com/”?
Oh third question, related to my “No. 2” above. In terms of deleting the “WP Directory” I asked if every file and folder should be deleted under the folder entitled “mysiteurl.com/”, but that folder is a sub folder of my “root” folder, there are other subfolders in the root (cgi-bin, Stats,etc..) do I delete all of those too?
@Juice –
1) There could be infected code in the database, and I am not certain what all WP import grabs. Usually though with that the biggest concern would be iframes and scripts that were injected into the actual posts. The only entries that would be of concern for re-entry by the hackers would be in wp_options or wp_users.
2) & 3) I would delete everything that is accessible from the web, or everything under what is known as your “web root”. In most cases this will be a directory named either yourdomain.com, public_html, web, or httpdocs, although there are other possibilities. You should not have to delete anything other than what is under that, unless you have moved the .htaccess, php.ini, or wp-config.php into the root.
Also, remember, backup *everything* first, and I would make a separate backup of your uploads directory, and then scan that and make sure that only images are inside of it. If so then you should be able to re-upload that to your fresh installation once you are done.
Thanks so much Michael. The different directories confuse me, naturally. I have a “webroot” file named mydomain.com, which is a sub folder of the main “directory” (if that is what its called). I was thinking I should delete every folder under the main directory (like the cgi-bin, stats,etc.). Earlier I did back up my uploads folder and looked through, but the files all looked normal to me- I am not sure I would recognize something malicious… I did do a WP import back up last week, maybe I should just reinstall WP and my theme from scratch, and then upload last week’s back up, then I only lose today’s post. Is it possible that the hackers hacked days ago, but their malicious activity only appeared today, for the first time? thanks again, you’re help has been invaluable!
Well, I deleted all my site directory files and started from scratch today. After installing WP and Theme from brand new downloads, I imported an old WP back up and an old theme back up. Then I added the /uploads/ file that I had backed up yesterday(post hack). I went about trying to rebuild my site until at 11 PM tonight, for the third day in a row, a new unauthorized WP User appeared in my admin panel. I deleted the user and began the password, secret key changes, while alerting my host once more to the problem. I honestly don’t know what to do anymore. I am lost.
I completely dumped my old wp files folders directory structure, the whole shabbang. How the heck can my fresh wp and plugins install still have malware links (months old) in my wp-includes/feed-rss2.php? according to a well known security host these bad links were pulled up by looking through my sites feed at the source code!
Kenneth, I would need to actually go into your site and do a scan and some checks to see what was up. I wish I could be more help but there are just too many things that could be going on to know without looking.
ok, well thanks for the speedy reply! ill be in touch soon
4 days ago 3 of my websites were infected with malware. One was picked up by Google and is now flagged for avoidance.
I have spent hours upon hours fixing this problem, yet every time the .htaccess files are reinfected with redirects to a Russian site of some description.
– When I cleaned the sites I changed all the passwords for FTP, site admin, and database. I deleted cookie logon function by resetting WP secret keys. I installed Bulletproof Security to protect .htaccess and my wp-config folder. This hasn’t worked, they just bypass it. The hackers also won’t let me resave the file when i delete their hack, instead making me have to download the file and then upload it clean.
– I thought the hack had come through filezilla. So I stopped cleaning through that and instead started using Go Daddy file manager to clean the reinfected .htaccess flles. But no, reinfection within 7 hours. Go Daddy, as per usual, don’t have a clue what I should even be looking for.
– I also installed site DB backups but that didn’t make a difference. Neither did the plugin upgrades or WP upgrades I did when the sites were clean, which they were because i scanned them at sucuri.net.
– I have scanned every line of php for bad code using the advice on forums like this one and blogs, etc. I can’t see anything untoward and just don’t know what to do. As far as I can see this is purely the .htaccess file that is getting attacked. I have even completely deleted the file yet they keep putting a new one in.
– one thing i find strange is that it only attacked these 3 sites. I have 3 other WordPress sites on the same hosting that it hasn’t affected. I have a feeling it got to my root site first and worked into the others, but then I don’t know how these things work so i am probably wrong. Could there be one file in the root that is triggering all this?
If you have any clue what i should be looking for I would greatly appreciate any advice. I can’t afford to shed out $100 each for a site clean, hell, the sites are more sentimental than valuable.
Thank you.
Just discovered a site I redesigned has been injected – AVG warning appeared on Thursday, Oct. 13. Need to present site at the end of the month – can someone please contact me at dgolden@nasbp.org for assistance and quote? Site is suretyinfo.org. Thanks.
Thanks for the helpful info. Too bad this is a continuing problem.
Mike
hi michael, i really need your help, i got redirect blog problem. After someone type keyword in google browse n click my blog (wordpress), he will get my blog just a few second. after that, he will redirect to other website, what i’ve to do to solve this problem? i’m really happy if you give me the solution n send to my email: iyan_41@yahoo.com
Cleaning a 3 GB space in my host is killing me, and i can not find the source of infection for 3 weeks. Damn. Thank you for the post, now i have few more places to look 🙂
Just wanna say a big thank you to Michael for rescuing my blog. Excellent service at a fair price too!
Ah, Michael, you’re a lifesaver! Thanks for the handy tip. I was NOT looking forward to editing 103 pages to correct those silly apostrophes!
@Jordan, No problem, glad I could help. 🙂
this is very good info however i was wondering if you had any insight on special characters showing up in posts? i have searched high and low, got some instruction on how to delete them from my cpanel with no success. help! if you can. I do not want to delete my whole blog of two years work.
Cathy, that is something that I can usually fix, but how I fix it depends on how they got there in the first place and what the underlying cause of the character conversion is, and what, if anything, you did already to attempt to fix them. Feel free to hit me up via my contact form if you need help cleaning them out.
Hi everyone,
I really need help! I have a new website for my business, few days ago I noticed on the footer the line sayin sintax error footer.php line 3. I checked with an antivrus plugin and coming up with virus, so I update wordpress, I change all my passwords and delate all the pages,plugin,post,pictures,everything (i have a backup)
But still there is that line and the home page layout is messed up.
What can I do? Do i have to delate something from the cpanel?
Sorry I am very new to these things!
Thak you !
Martina
Hi,
one of my blogs is infected by Trojan.JS.Iframe.ARU (Engine A)
Does anyone know if there is a plugin that can helps me to remove or check the wordpress installation ?
Thanks
All my sites got infected with a decode_base64 script in the last 3 weeks and I am trying to save everything. It’s a slow process. This article took me a while to find, but I am hoping the tips will help.
I tried to manually clean the php files from Filezilla, and like so many others, within hours they were modified again. Now it seems every “<?php" statement has the script added to it, as many as 50 lines of code to update in many files.
I am hoping to get into my site to export the database as xml, so I can rebuild it on a new host. I do have an SQL export, but not a WP export unfortunately.
It just proves you can never have enough backups, and in this case ALL my domains on the host caught the same infection.
@Tony – regarding all of your sites on the same host, with most shared hosting accounts that let you host multiple sites under one account that is what will happen… one gets hit, they all get hit.
It’s funny but the site i’m trying to fix is hosted on your recommended host Hostgator.
So much for that.
how do u copy your images from your uploaded files (to back up your hacked site), if u can t have access any more to your admin in wordpress?
Joe, unfortunately security holes in hosting isn’t the only way that hackers can get in, so even on the best host if there is an old back door or vulnerable script on the site, or if someone with ftp access to the site gets a virus, the sites can still get hacked.
@shalhevet – you need to use ftp to access the uploads directory and download them all. Make you you verify there is nothing but images in the folder before re-uploading them to the cleaned site as well.
Great info thanks! I had an iframe injection virus of some sort – every instance of index.php had an iframe appended.
Thanks mate, you helped me fix the blog that’s linked above. Great stuff.
how i can clear this harm AS8426 (CLARANET)?
please help